Vendor risk is no longer a side concern for organizations relying on third parties. As businesses expand their vendor networks, manage increased regulatory demands, and respond to real-time threats, a proactive approach to vendor risk management (VRM) has become essential.
It’s time for risk, IT, and procurement leaders to align vendor oversight with organizational strategy and collaborate on productive vendor risk management strategies that protect and create value.
Why Vendor Risk Management Matters Now
Vendor risk management governs organizations’ understanding, framework, and management of all risks resulting from relationships with vendors, third parties, service providers, and suppliers. Key risk types include cybersecurity attacks, noncompliance, financial and reputational penalties, data breaches, supply chain disruption, and more.
With global business ecosystems more interconnected than ever, the average organization works with dozens or hundreds of vendors, many of whom have direct or indirect access to sensitive systems and data.
Recent studies highlight just how pressing these risks are:
- 61% of organizations have experienced a third-party data breach or security incident in the past 12 months.
- 98% of companies worldwide have at least one vendor with a documented security breach.
- A single vendor failure, like 2024’s Crowdstrike outage, can ripple through critical sectors including airports, hospitals, financial markets, and government.
Understanding and managing vendor risk is crucial for ensuring compliance and safeguarding business continuity and reputation.
Demystifying Vendor Risk
Not all vendors pose equal risk.
- Critical vendors: Directly impact operations, financial stability, or corporate security. Examples include cloud service providers, key software developers, or payment processors. Failure in these relationships can result in data loss, extended downtime, or customer dissatisfaction.
- Non-critical vendors: May impact operational efficiency but are easier to replace without major disruption. Examples include office supply companies, marketing agencies, or local contractors.
Classifying your vendor base with a risk lens helps focus resources on oversight where it matters most.
The Expanding Scope of Vendor Risk Management
Modern VRM extends far beyond traditional contract reviews. Today’s risk surface includes:
Key Risk Domains
- Cybersecurity: 62% of organizations rank this as their top VRM focus.
- Geopolitical threats: 33% see growing exposure due to global supply chains.
- Operational resilience: 32% prioritize continuity and disaster recovery.
- Data privacy: 29% highlight rising data protection laws and compliance obligations.
Emerging factors such as AI risk, subcontractor risk, and concentration risk (over-reliance on a small number of core vendors) further complicate the picture.
Proliferation of Regulations
Organizations must comply with established frameworks like GDPR, CPRA, and HIPAA, but also anticipate new laws such as DORA, EU AI Act, and NIS2. This means VRM must evolve quickly to stay ahead of shifting compliance expectations and cross-border data obligations.
Top Challenges in Vendor Risk Management
Even seasoned teams encounter common pitfalls:
Contractual Complexity
Many organizations struggle to maintain consistency in vendor contracts. Missing or inadequate clauses related to cybersecurity, termination rights, or data access can leave organizations exposed.
Visibility Gaps
70% of risk managers feel they lack full visibility into their supplier risk landscape. This makes it difficult to track evolving risks, especially as vendor networks grow large and complex.
Supply Chain Complexity
End-to-end monitoring remains a challenge, particularly in diversified or global supply chains where risk signals can be hard to aggregate.
Dynamic Risk Profiles
Vendor risks are not static. Changes in market health, regulatory environment, or even vendor leadership can alter a provider’s risk posture overnight.
Accountability and Governance
Disconnected protocols, unclear ownership, and ad hoc communication hamper effective vendor oversight and incident response.
Key Metrics for Vendor Risk Insights
Data-driven VRM relies on meaningful metrics to inform strategy and prioritize action. Consider these KPIs:
- Percentage of major cyber incidents traceable to vendors: Quantifies external attack surface risk.
- Number of vendors at financial risk (e.g., bankruptcy or major distress): Exposes resiliency or operational vulnerabilities.
- Count and percentage of vendors violating regulatory requirements: Helps spot compliance weak points.
- Percentage of critical vendors performing unique (non-redundant) functions: Reveals single points of failure.
- Vendor access to critical assets such as crown jewels: Exposes points of failure from which it’s difficult to recover.
- Growth in vendor population and the share of critical vendors in that group: Demonstrates vendor sprawl and risk surface expansion.
Regular tracking of these metrics gives compliance leaders early warning signals and a concrete basis for executive reporting.
The Continuous Monitoring Imperative
Modern organizations recognize that vendor risk is not a one-and-done exercise. Risk profiles change as vendors grow, merge, or adapt to new markets.
- Threat actors evolve strategies and exploit fresh vulnerabilities in vendor ecosystems.
- Regulatory pressure intensifies, requiring demonstrable, real-time monitoring capabilities and documented response protocols.
- Automated risk platforms, third-party ratings solutions, and deep-dive audits are increasingly essential to maintain visibility and resilience across the vendor landscape.
Strategies to Strengthen Your VRM Program
For a practical approach to enhanced vendor risk management, leaders can take the following steps:
- Centralize vendor inventory: Build and maintain a live register of all vendors, their roles, risk ratings, and criticality.
- Standardize contracts and controls: Adopt contractual frameworks that include clear obligations, incident disclosure, audit rights, and defined offboarding procedures.
- Invest in technology and automation: Use AI-enabled solutions for risk assessments, automated questionnaires, and continuous monitoring.
- Embed cross-functional governance: Draw on compliance, IT, procurement, and legal teams to create a governance model with defined ownership and escalation paths.
- Cultivate executive support: Ensure executive sponsorship for VRM by framing risk management as an enabler of growth and resilience.
- Leverage data and analytics: Use dashboarding and regular risk reviews to inform business decisions and report progress to stakeholders.
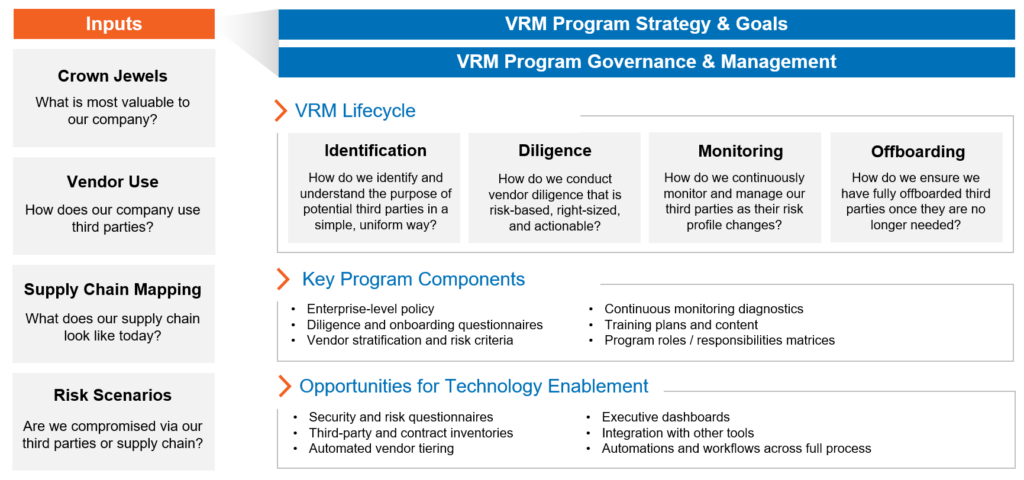
Building a Resilient Vendor Risk Management Program
Vendor risk will keep rising as organizations deepen reliance on external partners and as regulatory obligations expand. The organizations that thrive will move beyond reactive approaches and instead build integrated, proactive VRM programs anchored by real-time data, cross-functional collaboration, and smart automation.
The result is not just improved compliance, but a more resilient business with increased strategic agility. To collaboratively build a vendor risk management program that’s right for your organization, contact CrossCountry Consulting.

