Legacy controls fail in emerging-risk environments.
When disruption is around every corner and incoming from every imaginable vector, your enterprise risk management (ERM) apparatus must be always-on. But that’s hardly the case, as shown in a February 2022 webinar from AuditBoard and CrossCountry Consulting.
Just over 26% of surveyed respondents stated they had a “mature” enterprise risk management program – the other three-quarters of ERM programs were in varying states of nonexistence or adolescence.
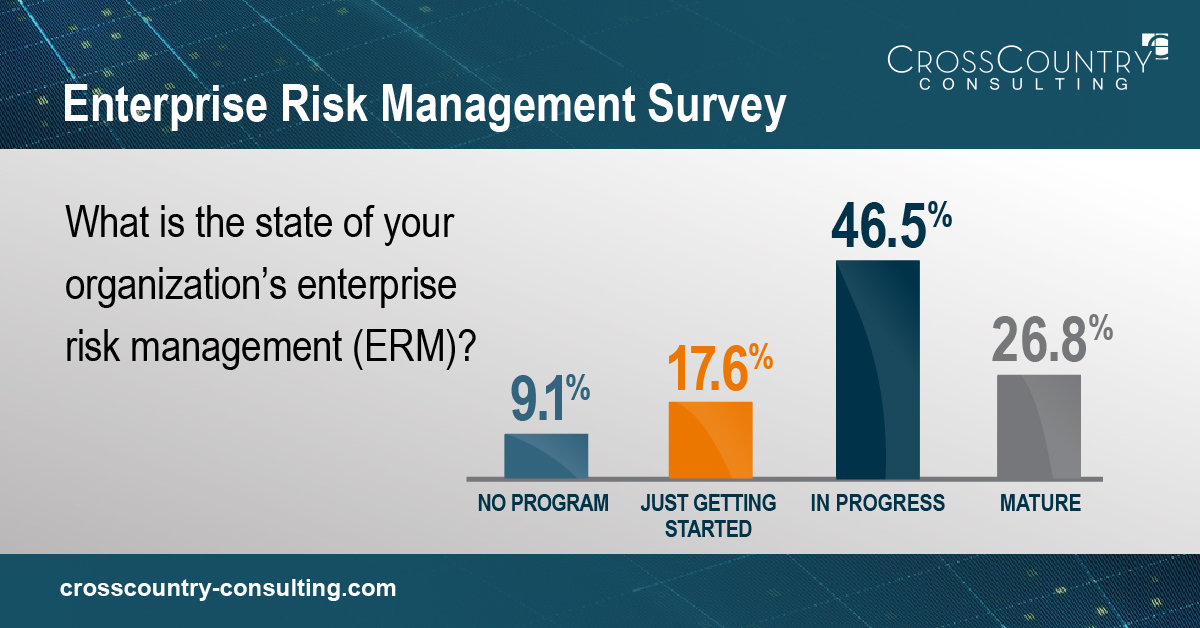
That’s one key insight from the webinar. Two apparent drivers of current-state ERM challenges are driving a risk wedge through organizations:
- Disruption everywhere.
- Hyperdispersion.
What Is Disruption Everywhere?
Disruption everywhere is the concept (and the reality) that disruption does not turn off and it’s all around us. Risk velocity and volatility are thus the new norm, and security perimeters continue to expand outward and into every facet of business and personal lives.
The result is that organizations are inherently more often than not on their back foot. Their ability to predict and react to disruptions – be it supply chain issues, a global pandemic, inflation, a Great Resignation, cyber warfare, etc. – is constrained by the internal or external resources they have at their disposal at any given moment.
Faced with new technologies displacing legacy systems, every new integration, platform, and digitally enabled tool raises the ante on today’s table stakes. They’re a necessity to keep pace with disruptive technological forces and growing employee demands, but they invite a ripple effect of potential downstream disruptions:
- Lack of adoption from key stakeholders.
- Immature risk controls.
- Influx of unstructured data into an already poor data infrastructure.
- Unclear cross-functional integration roadmap.
- Machine learning bias.
- Employee skepticism.
- Many more.
Ultimately, trying to account for disruption may lead to a bigger risk gap.
Poor risk management hygiene will simply be replicated and entrenched if proper controls and processes are not established alongside the introduction of new technology. Luckily, roughly 85% of survey respondents were to some degree confident in their abilities to close their organization’s risk gap.

What Is Hyperdispersion?
Hyperdispersion is the decentralization of people, power, capital, infrastructure, processes, and communications. The very things businesses need to operate successfully are now stretched across the globe.
With the rise of distributed workforces, remote agile operating models, automated bots, and the gig economy, how business is conducted is dispersed over an array of timezones, software tools, methodologies, employment types, and infrastructures.
The entry point for a major cyber event exists along this entire spectrum. Risk has endless permutations of vectors through which to seep.
It’s no surprise, then, that it takes up to 280 days on average for an organization to become aware of a cyber breach. Once detected, it takes another 80 days to contain it. The full lifecycle of a breach can swallow an entire year: data, money, reputation – gone.
 On a macro level, the fragility of global supply chains adds another layer of risk uncertainty. Opacity in the regulatory environment, too, makes it difficult for organizations to mount a successful, predictable, future-ready response to dispersed risk events largely out of their control.
On a macro level, the fragility of global supply chains adds another layer of risk uncertainty. Opacity in the regulatory environment, too, makes it difficult for organizations to mount a successful, predictable, future-ready response to dispersed risk events largely out of their control.
At a market level, the number of IPOs has never been higher, with more than 2,000 firms going public in 2021 and a full pipeline of IPOs for 2022 as well. Competitive disruptions in the form of new players perpetually shift the risk calculus of organizations.
So how are businesses dealing with the variety of risk demands evident today?
A sliver of survey respondents were unsure, and more than 7% admitted to handing risk poorly. Roughly 90% stated they were “average,” “good,” or “excellent.”
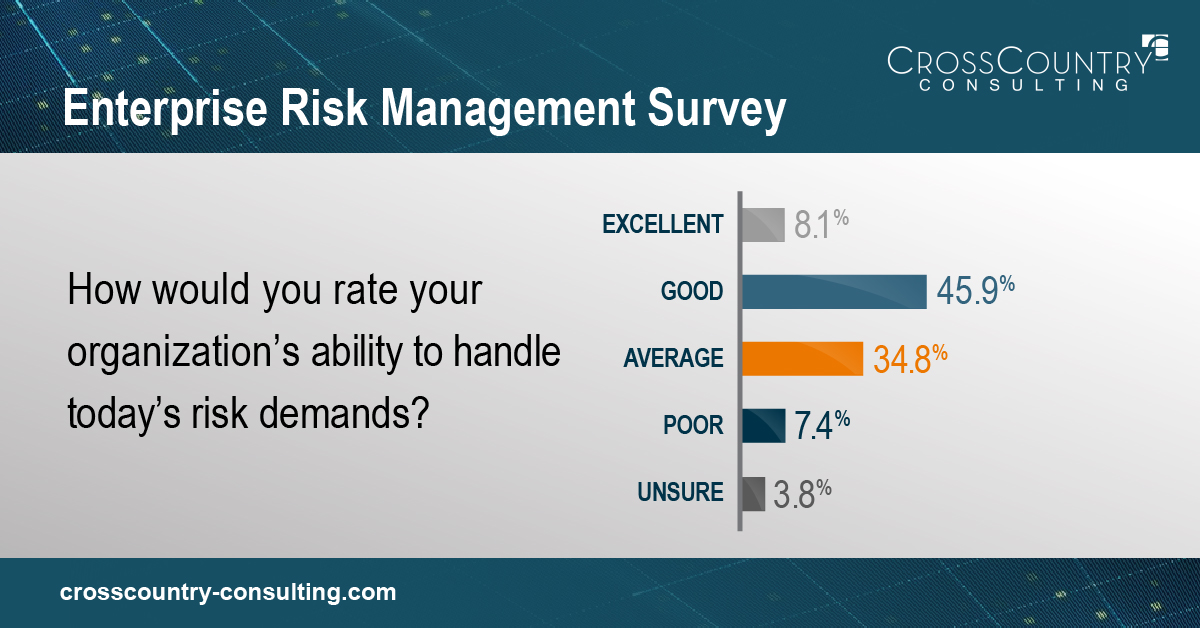
The range of responses suggests firms are well-intentioned and well-informed, but they may lack the cohesive strategy and resources to be fully resilient in the face of dispersed, disruptive threats.
Integrated Risk Management Solutions
Point solutions to enterprise risk challenges can provide piecemeal security. They can temporarily patch up risk resilience gaps in time for audits or in conjunction with new software implementations.
But they may not amount to the enterprisewide, comprehensive risk defense that’s needed in light of hyperdispersion, perennial disruption, and myriad other obstacles.
And businesses are already notably concerned with their internal capability to close risk gaps, with siloed teams (26.2%) and lack of capacity (29.3%) plaguing progress.
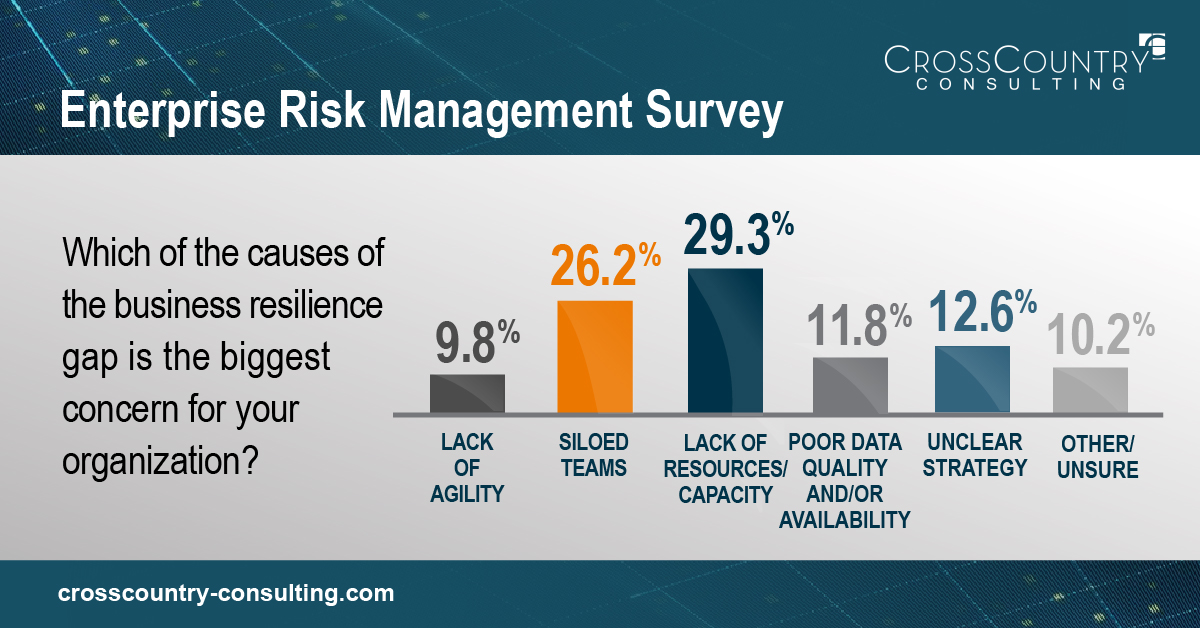
Businesses must accept a few key facts:
- Risk is inevitable.
- Expect to fail and to fail fast.
- Efficient, proactive response activity is the only way to mitigate and monitor emerging risks.
To accomplish the level of ongoing security needed to thwart multivariate threats, integrated solutions are a must. These solutions can take the shape of:
- Development and clarification of 1st, 2nd, and 3rd lines of defense throughout the business (Management, Risk Management & Compliance, and Internal Audit).
- A mature cross-functional risk assessment and risk management framework.
- Risk resilience operational governance.
- Engagement and alignment with all assurance functions (Compliance, Internal Audit, ERM, InfoSec, Sox Controls, Legal).
- Implementation of threat-based risk assessments and modeling, helping the organization understand specific threat actors, methods, and defense opportunities.
Additionally, key compliance and audit stakeholders are seeking to combat hyperdispersion with advanced cyber programs that go beyond organizational frameworks or intangible methodologies. They want firm, targeted action and triggers that level-up their defense strategies. They want offensive security, including:
- Red teaming, a multi-layered attack simulation.
- Adversary emulation, which mimics threat actors and their objectives.
Legacy controls are asleep at the wheel. It takes centralized risk management to help impede decentralized risk.
For strategic support on your risk resilience journey, contact the cyber and risk management experts at CrossCountry Consulting today.